Cloudflare has announced its 2023 Q4 DDoS report – which showed that DDoS attacks reached new heights in 2023. This …


Cloudflare has announced its 2023 Q4 DDoS report – which showed that DDoS attacks reached new heights in 2023. This …

In 2024, the telecommunications industry will continue to focus on technologies such as cloud computing, standalone 5G, AI, and the Internet of Things (IoT) to offer better speed, scalability, and innovation.

NETSCOUT SYSTEMS, INC. (NASDAQ: NTCT), a leading provider of performance management, cybersecurity, and DDoS protection solutions, has released findings from …

Emad Fahmy, Systems Engineering Manager Middle East at NETSCOUT, outlines how educational institutions can prevent and defend against DDoS attacks. …

Building a Safer Stronger Internet with Adaptive DDoS Suppression.

Netscout announces Omnis AIF for smarter automated DDOS attack blocking.

DDoS Attack Trends for Q1 2022: Cloudflare Report.

NETSCOUT Op-Ed: Keeping Disruptive DDoS Attacks at Bay.

A10 Networks’ Threat Research Detects and Tracks Origins of DDoS Weapons; Observes Over 15 Million Weapons.

Since mid-February, the NETSCOUT Arbor Security Engineering and Response Team (ASERT) has been monitoring the situation in Russia and Ukraine and the ongoing high-profile DDoS attacks targeting organisations, networks, applications, and services in Ukraine.

A10 Networks: Why Attackers are Focusing on Low-Volume Persistent DDoS Attacks.

Global Lockdowns May Limit COVID-19, But Not DDoS.

Preventing SSDP-based DDoS Attacks.

A return to pre-pandemic working practices is unlikely to happen. To learn more about the impact on networks and cyber security that COVID-19 has had on service providers, A10 Networks commissioned a survey and the results from the Middle East provide interesting insights. A large proportion of the senior IT professionals that we surveyed were adamant that the workplace won’t snap back to how it was before COVID-19, and that they expect and are preparing for a hybrid approach to working practices. The pandemic significantly raised awareness around the resiliency of the network and the robustness of security, and going forward, subscribers and enterprises expect much stronger security from their communications service providers and will demand more in their SLAs and expand to other types of service providers to get this commitment.

Qrator Labs, a DDoS mitigation and continuous availability service provider, partners with HUAWEI CLOUD Marketplace to provide top-notch DDoS attacks mitigation service for wide range of customers within the Huawei ecosystem.

Defending Against Increasing DDoS Attacks in the Light of COVID-19 and 5G.

For the first time in history, we observed the annual number of DDoS attacks cross the 10 million threshold, with NETSCOUT’s ATLAS Security Engineering and Response Team (ASERT) observing 10,089,687 attacks over the course of the year.
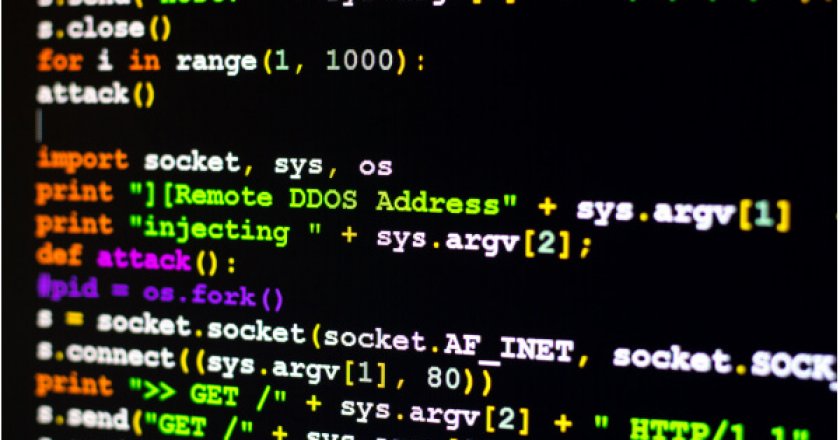
Security correspondent Daniel Bardsley speaks to industry experts to discuss the current state of DDoS attacks and how organisations can steer clear.
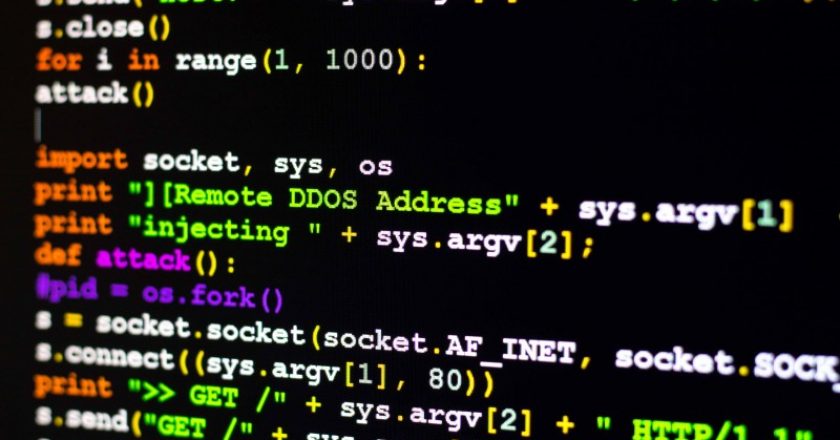
Zain Group’s fully owned global services subsidiary, Mada Communications, has announced that it will be rolling out a next-generation, cloud-ready DDoS mitigation technology in partnership with application security experts F5 Networks.

Though distributed denial of service attacks have been around more than two decades, recently we have seen a spate of DDoS attacks that have increased in complexity and variability.